I use this app to pay my gas bill and to look at statistics about my gas consumption. My buddy Adam Logue and I sat down one night to figure out how it worked. Using Burp Suite, we intercepted the requests being made from the app.
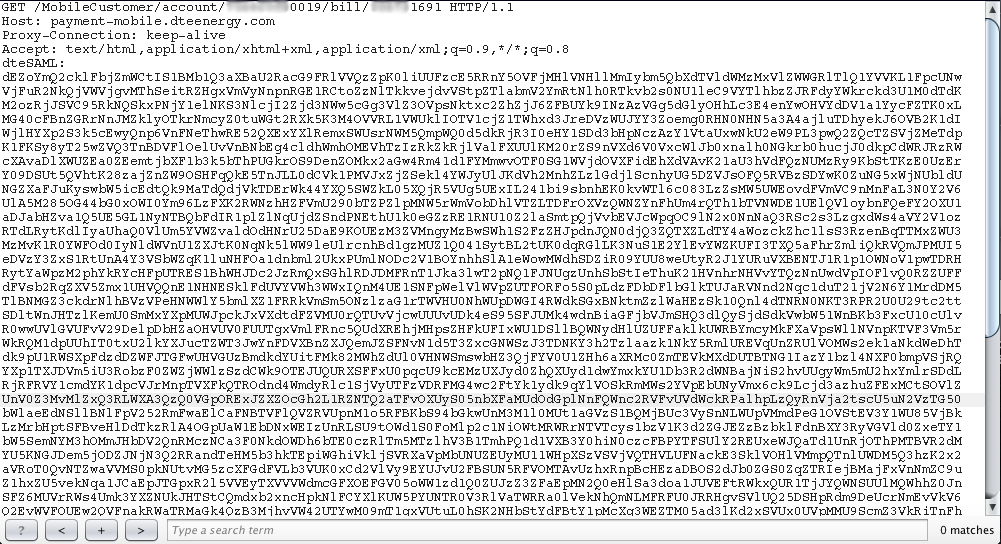
The “View Billing Statement” button in the mobile app brought up the statement in a pdf document , just like the one that comes in the mail. The request looks something like this:
In the GET request to grab the billing statement, there are two numbers in particular that interested us. The first being the account number and the second being the billing statement number. It wasn’t hard to identify each one, as they were both included in the billing statement itself. For this write-up we have blurred out all but the last four digits of each to respect everyone’s privacy.
A normal request will pull up a familiar billing statement with information like this:
The billing statements contain personal information including first and last name, full address, account number, billing statement number, and other goodies.
So how is this exploited? Lets see if the request is vulnerable to insecure direct object references! The screenshots below are from the proof of concept video we sent DTE.
With permission from my parents, we were given access to their DTE account to use as a second set of valid account and statement numbers. We tried the request again, this time swapping my billing statement number in our original request with my parent’s. Notice the account number in the request is still my account.
The response?
My mom’s bill.
After we discovered the vulnerability, we compiled a proof of concept video detailing the discovery. We reached out to [email protected], and also over LinkedIn to a few of the higher up IT and InfoSec professionals. We were contacted back the very next day by Don VanDePutte, Senior IT Security Engineer at DTE. He was very professional and notified the appropriate individuals immediately. DTE was very quick in fixing this vulnerability and didn’t waste time, rolling out a patch in less than a week.
Disclosure Timeline
6/9/2015: Attempted contact via LinkedIN and [email protected]
6/10/2015: Received reply back from Don VanDePutte, Senior IT Security Engineer, requesting PoC
6/10/2015: Sent PoC via email to Don
6/10/2015: Received acknowledgment back regarding PoC with appropriate individuals notified
6/15/2015: Received update that the vulnerability has been patched
6/15/2015: Fix Confirmed
A special thanks goes out to DTE Energy for fast communication and quickly patching the vulnerability, Adam Logue for helping me find the vulnerability, and my Parents for giving permission to use their account.